Member Article
Cloud Migration and Remote Work Gives Rise to New Era of Malware, Highly Evasive Adaptive Threats (HEAT)
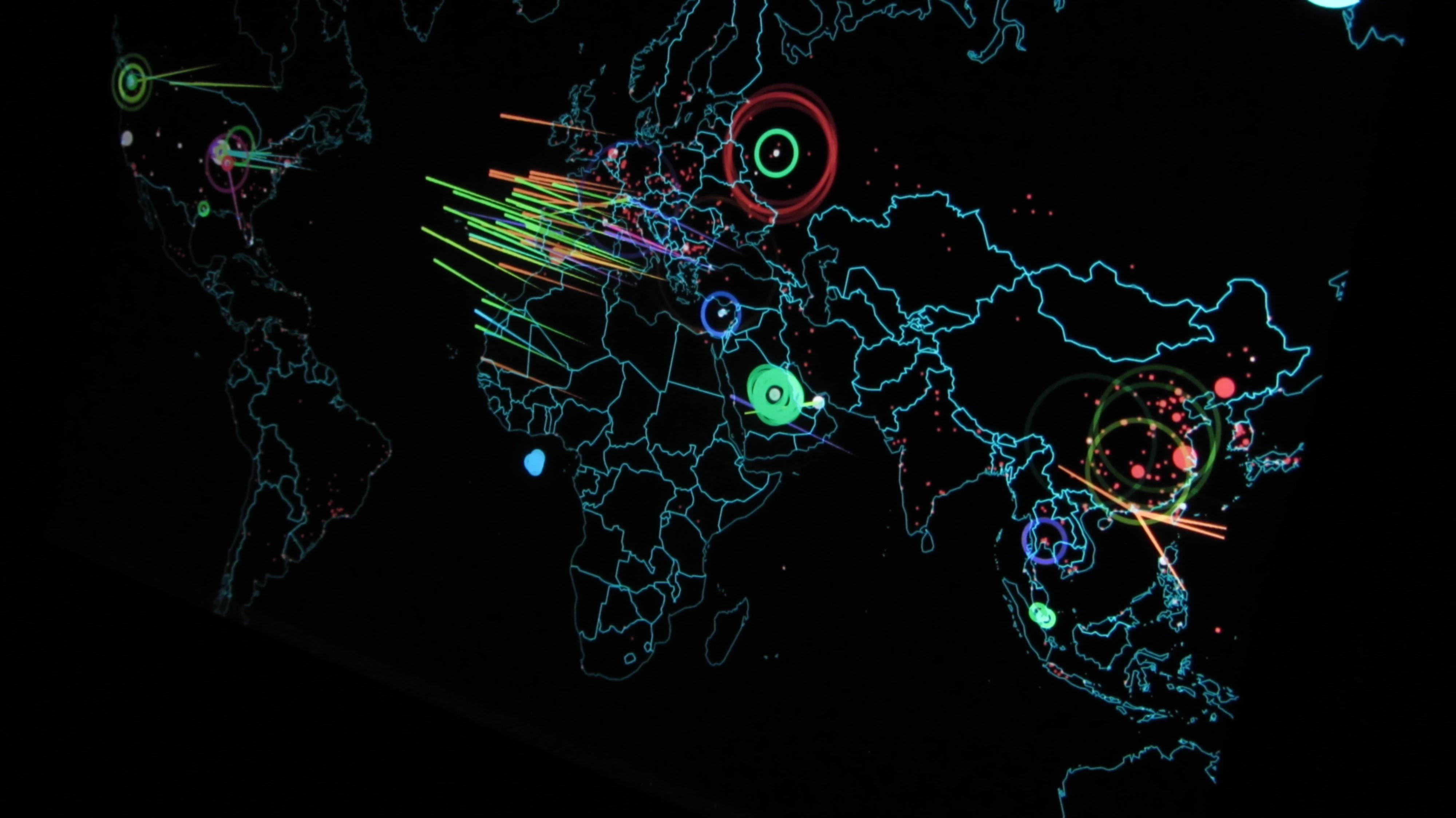
A surge in cyberthreats, termed Highly Evasive Adaptive Threats (HEAT) that bypass traditional security defences has been identified. HEAT attacks are a class of cyber threats targeting web browsers as the attack vector and employs techniques to evade detection by multiple layers in current security stacks including firewalls, Secure Web Gateways, sandbox analysis, URL Reputation, and phishing detection. HEAT attacks are used to deliver malware or to compromise credentials, which in many cases leads to ransomware attacks.
In an analysis of almost 500,000 malicious domains, The Menlo Security Labs research team discovered that 69 per cent of these websites used HEAT tactics to deliver malware. These attacks allow bad actors to deliver malicious content to the endpoint by adapting to the targeted environment. Since July 2021, the research has seen a 224 per cent increase in HEAT attacks.
Following the abrupt move to remote working in 2020, every organisation had to pivot to a work from anywhere model and accelerate their migration to cloud-based applications. With 75 per cent of the working day spent in a web browser, it has quickly become the primary attack surface for threat actors, ransomware, and other attacks. The industry has seen an explosion in the number and sophistication of these highly evasive attacks and most businesses are unprepared and lack the resources to prevent them. Cyber Threats are a mainstream problem and a boardroom issue that should be on everyone’s agenda. The threat landscape is constantly evolving, ransomware is more persistent than ever before, and HEAT attacks have rendered traditional security solutions ineffective.
“Highly Evasive Adaptive Threat (HEAT) attacks evade existing security defences by understanding all the technology integrated into the existing security stack and building delivery mechanisms to evade detection,” said Senior Analyst, John Grady. “Organisations should focus on three key tenets to limit their susceptibility to these types of attacks: shifting from a detection to a prevention mindset, stopping threats before they hit the endpoint, and incorporating advanced anti-phishing and isolation capabilities.”
This was posted in Bdaily's Members' News section by Contributor .



 How advancements in technology are shaping the future of the economy in North East England
How advancements in technology are shaping the future of the economy in North East England
 South Yorkshire Craftsmanship and Innovation: A Tale of Heritage and Growth
South Yorkshire Craftsmanship and Innovation: A Tale of Heritage and Growth
 Demystifying Degree Apprenticeships
Demystifying Degree Apprenticeships
 Industry-focused apprenticeships pave the way for a bright future in science manufacturing
Industry-focused apprenticeships pave the way for a bright future in science manufacturing
 What’s the best hosting plan for a business website?
What’s the best hosting plan for a business website?